Breaking Down Termite Ransomware: Infection Methods and Detections

The Termite ransomware group, known for its stealthy and destructive attacks, has recently made headlines after claiming supply chain vendor Blue Yonder as one of its victims. Now, security researchers have linked Termite to a surge in exploit activity targeting a previously patched — but now re-emerging — vulnerability in Cleo’s LexiCom, VLTransfer, and Harmony file transfer software.[1]
The attacks began on December 3, 2024, with researchers at Huntress Labs identifying at least 10 victims across industries such as consumer products, trucking, shipping, and food services. However, a broader search for vulnerable, Internet-exposed Cleo systems suggests the actual number of compromised organizations may be higher. Security firm Rapid7 has also observed post-exploit activity involving the Cleo vulnerability (CVE-2024-50623), an unauthenticated remote code execution (RCE) flaw affecting Cleo Harmony, VLTrader, and LexiCom. Despite Cleo releasing a patch in October, researchers found that even fully updated systems running version 5.8.0.21 remain vulnerable. With over 4,200 businesses relying on Cleo software — including major brands like New Balance, Barilla America, and TaylorMade. Additionally, Termite’s attack on Genea, an Australian fertility services provider, led to the exfiltration of approximately 940 GB of sensitive patient data, including medical histories and contact information. These incidents highlight Termite’s ability to inflict severe financial, operational, and reputational damage across multiple industries.
In the following sections, the Splunk Threat Research Team will break down the MITRE ATT&CK® tactics and techniques identified during the Termite Ransomware analysis, providing insights into Splunk detection coverage and testing methodologies.
Analysis
Inhibit System Recovery (T1490)
Like other ransomware strains, Termite Ransomware attempts to delete shadow copies on the compromised host by executing the vssadmin.exe delete shadows command, as shown in Figure 01. This tactic is commonly used by ransomware operators to prevent victims from restoring files through Windows' built-in Volume Shadow Copy Service (VSS). By erasing these backups, attackers eliminate an easy recovery option, increasing the likelihood that victims will pay the ransom to regain access to their encrypted data.

Figure 01: Delete Shadow Copy
Service Stop (T1489)
Termite Ransomware attempts to terminate multiple Windows services, particularly those related to security software and backup applications. This tactic ensures that critical protection mechanisms are disabled, reducing the chances of detection and mitigation. By shutting down backup-related services, the ransomware increases the likelihood of corrupting or preventing access to backup files, making recovery more difficult.
The table below lists the Windows services that Termite Ransomware attempts to terminate or disable. Figure 02 displays a code snippet from the malware, showcasing the function responsible for stopping these services via the ControlService() API. During enumeration, if a targeted service is active, the ransomware invokes the SERVICE_CONTROL_STOP control code to forcibly shut it down. This tactic ensures that security software and backup solutions are rendered ineffective, preventing detection and disrupting potential recovery efforts. By eliminating these defenses, Termite maximizes the impact of its encryption process, leaving victims with no easy way to restore their files and increasing pressure to pay the ransom.
| HvHost, vm3dservice, vmcompute, vmicguestinterface, vmicheartbeat, vmickvpexchange, vmicrdv, vmicshutdown, vmictimesync, vmicvmsession, vmicvss, vmms, vss, sql, svc$, memtas, mepocs, sophos, veeam, backup, GxVss, GxBlr, GxFWD, GxCVD, GxCIMgr, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, RTVscan, QBFCService, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, YooBackup, YooIT, sophos, stc_raw_agent, VSNAPVSS, VeeamTransportSvc, VeeamDeploymentService, VeeamNFSSvc, veeam, PDVFSService, BackupExecVSSProvider, BackupExecAgentAccelerator, BackupExecAgentBrowser, BackupExecDiveciMediaService, BackupExecJobEngine, BackupExecManagementService, BackupExecRPCService, AcrSch2Svc, AcronisAgent, CASAD2DWebSvc, CAARCUpdateSvc |
Figure xx: Targeted Windows Services

Figure 02: Kill Security and Backup Windows Services
Impair Defenses: Disable or Modify Tools (T1562.001)
In addition to stopping security and backup-related Windows services, Termite Ransomware also attempts to terminate processes associated with virtual disks, databases, emails, and document editors. This ensures that critical files are not in use, allowing the ransomware to encrypt important data on the compromised host without interference.
The table below is the list of processes it tries to kill and the Figure 03 is the screenshot of the Termite ransomware function responsible for this technique.
| vmmem.exe, vmwp.exe, sqlservr.exe, sql.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, agntsvc.exe, isqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, encsvc.exe, firefox.exe, tbirdconfig.exe, mydesktopqos.exe, ocomm.exe, dbeng50.exe, sqbcoreservice.exe, excel.exe, infopath.exe, msaccess.exe, mspub.exe, onenote.exe, outlook.exe, powerpnt.exe, steam.exe, thebat.exe, thunderbird.exe, visio.exe, winword.exe, wordpad.exe, notepad.exe |
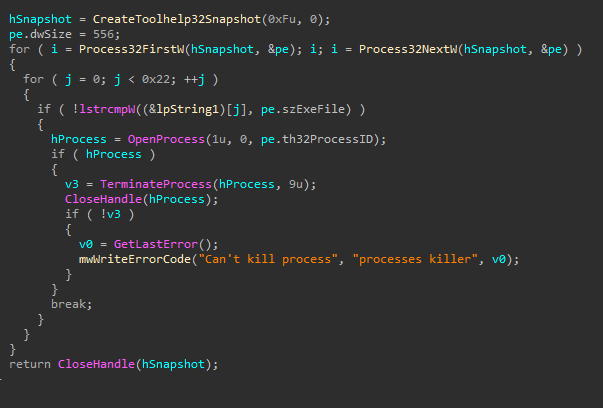
Figure 03: Process termination
Data Encrypted for Impact (T1486)
Termite Ransomware includes several configurable parameters that allow it to perform specific tasks or encrypt files in designated locations. These parameters enhance its flexibility and effectiveness during an attack. The table below outlines the primary parameters used by this malware:
| Parameters | Description |
|---|---|
| --debug=<debug_log_path> | Generate debug logs |
| --onefile=<encrypt_file_path> | Encrypt a specific file. |
| --shares=<net_share_path> | Encrypt a specific net share path |
| --paths=<remote_drive> | Encrypt a specific remote drive path |
Termite Ransomware is designed to aggressively encrypt data across the compromised system. It scans multiple directories and storage locations to maximize damage and impact. By systematically targeting valuable files in various paths, the malware ensures widespread disruption within the affected environment. Below is a list of key locations that are commonly targeted for encryption:
File encryption in net share
Figure 04 shows a screenshot of Termite Ransomware's code, which systematically enumerates files and data within network shares for encryption, specifically targeting the ADMIN$ share. ADMIN$ is a hidden administrative Windows share that grants remote access to the system directory (C:\Windows). It is primarily used by IT administrators for remote management, software deployment, and troubleshooting. By encrypting files within ADMIN$, Termite Ransomware ensures maximum impact, disrupting not only the local system but also potentially spreading across networked devices, increasing the severity of the attack.
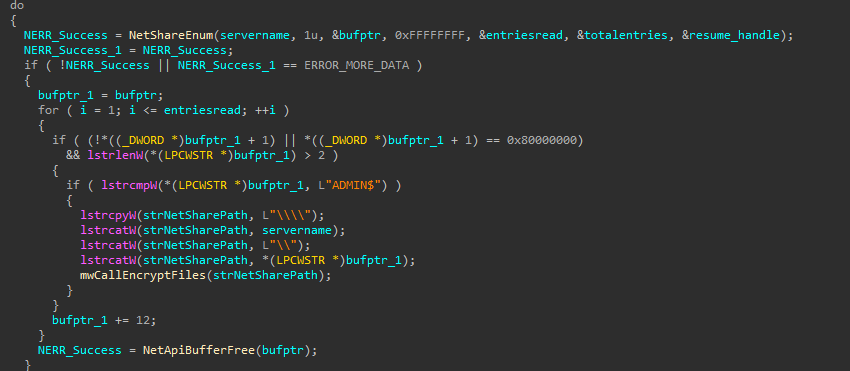
Figure 04: Encryption in Admin Share
Figure 05 shows the screenshot of the functions code that uses WNetOpenEnum() and WNetEnumResourcesW() to enumerate network shares and mapped drives across the compromised system or network. These functions allow the ransomware to identify accessible shared folders, network drives, and other resources that could contain valuable data. By calling WNetOpenEnum(), Termite initiates the process of discovering available network resources, and with WNetEnumResourcesW(), it enumerates and lists these shared directories or drives. This technique enables the ransomware to expand its reach beyond the local machine, targeting remote systems or servers connected to the same network.

Figure 05: Encryption in Net Share
File Encryption in Remote Drive
Figure 06 shows a screenshot of the Termite Ransomware code that enumerates drives and checks whether the drive type of each path is a remote drive. If the drive is identified as remote, the ransomware proceeds to enumerate all the files and data on the drive, marking them for encryption.
A remote drive refers to a storage device or network share that is not directly connected to the local machine but is accessible over a network. Common examples of remote drives include network shares (e.g., SMB or NFS shares) and mapped network drives that allow remote access to files stored on other machines or servers. By targeting remote drives, Termite can spread its encryption process across a larger network, potentially affecting multiple systems and increasing the overall damage of the attack.

Figure 06: Encryption in Remote Drive
File Encryption in Local Host
Termite Ransomware employs a strategy to maximize its encryption impact by targeting all possible root drives on the compromised system. In cases where it encounters a drive that might be protected or difficult to access, Termite uses the SetVolumeMountPoint() API. This API allows the ransomware to create mount points for specific volumes, essentially mounting them as accessible drives. By doing this, the ransomware can bypass some access restrictions and ensure it can fully encrypt data on those drives, even if they were initially harder to target.

Figure 07: File Encryption in Root Drives
Ransomware Notes
As part of its malicious behavior, Termite Ransomware generates ransom notes, as shown in Figure 08. These notes are deliberately placed across multiple directories on the compromised host, ensuring they are visible to the victim.
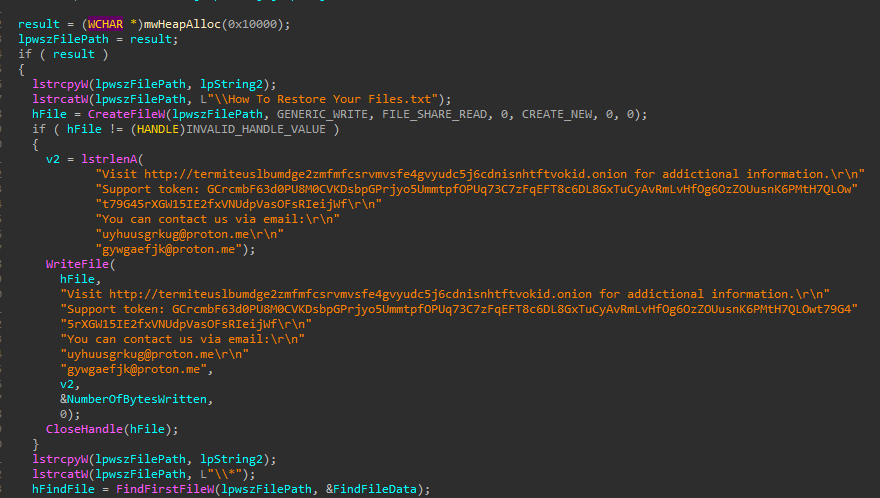
Figure 08: Ransomware Note Setup
Figure 09 illustrates how Termite Ransomware places ransom notes alongside encrypted files on the compromised host. This visual representation highlights the ransomware’s strategy of ensuring that victims encounter both the encrypted files and the ransom note, which serves as a constant reminder of the attack and the demand for payment to restore access to their data.

Figure 09: Termite Ransomware in Compromised Host
Splunk Security Detections
Ransomware Notes Bulk Creation
The following analytic identifies the bulk creation of ransomware notes (e.g., .txt, .html, .hta files) on an infected machine. It leverages Sysmon EventCode 11 to detect multiple instances of these file types being created within a short time frame. This activity is significant as it often indicates an active ransomware attack, where the attacker is notifying the victim of the encryption.
`sysmon` EventCode=11 file_name IN ("*\.txt","*\.html","*\.hta")
|bin _time span=10s
| stats min(_time) as firstTime max(_time) as lastTime dc(TargetFilename)
as unique_readme_path_count values(TargetFilename) as list_of_readme_path by Computer Image file_name
| rename Computer as dest
| where unique_readme_path_count >= 15
| `security_content_ctime(firstTime)`
| `security_content_ctime(lastTime)`

Figure 10: Ransomware Notes bulk creation Detection
Deleting Shadow Copies
The following analytic detects the deletion of shadow copies using the vssadmin.exe or wmic.exe utilities. It leverages data from Endpoint Detection and Response (EDR) agents, focusing on process names and command-line arguments. This activity is significant because deleting shadow copies is a common tactic used by attackers to prevent recovery and hide their tracks.
| tstats `security_content_summariesonly` count values(Processes.process) as process values(Processes.parent_process) as parent_process min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where (Processes.process_name=vssadmin.exe OR Processes.process_name=wmic.exe) Processes.process=*delete* Processes.process=*shadow* by Processes.user Processes.process_name Processes.parent_process_name Processes.dest | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)` | `deleting_shadow_copies_filter`

Figure 11: Deleting Shadow Copies Detection
Termite ransomware Analytic story consists of 6 detections to identify this threat.
IOC
| SHA256 | description |
|---|---|
| 30a8cf3e6863030c762b468bf48d679f3dd053a80793770443938fa18de89617 | Termite Ransomware |
Learn More
This blog is designed to assist security analysts, blue teamers, and Splunk customers in identifying Termite ransomware. It empowers the community to uncover related Tactics, Techniques, and Procedures (TTPs) employed by threat actors and adversaries. You can implement the detections in this blog using the Splunk Enterprise Security Content Update app or the Splunk Security Essentials app. To view the Splunk Threat Research Team's complete security content repository, visit research.splunk.com.
Feedback
Any feedback or requests? Feel free to put in an issue on Github and we’ll follow up. Alternatively, join us on the Slack channel #security-research. Follow these instructions If you need an invitation to our Splunk user groups on Slack.
Contributors
We would like to thank Teoderick Contreras for authoring this post and the entire Splunk Threat Research Team for their contributions: Michael Haag, Jose Hernandez, Lou Stella, Bhavin Patel, Rod Soto, Eric McGinnis, Patrick Bareiss, and Nasreddine Bencherchali.
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.